クリックできる目次
watchOS5.2リリース。香港と一部欧州での心電図対応と第2世代AirPodsに対応。また24件のセキュリティ問題に対応。アップデートすべきか否か、修正内容、アップデートのサイズと所要時間、更新後の不具合についてご紹介
watchOS5.2アップデートすべき?待つべき?
watchOS5.2は2番目の数字が変わるメジャーアップデートの位置づけとなります。 メジャーアップデートは不具合・バグの修正、セキュリティ問題への対応はもちろん新機能の追加などか含まれます。 実際、今回公式サイトの情報より、watchOS5.2では、Apple Watch Series 4に対する心電図アプリへの対応、不規則な心拍の通知、そして第2世代AirPodsへの対応と書かれています。 ただし、心電図アプリ、不規則な心拍の通知の対応は、香港とヨーロッパの一部の地域での対応と記載されており、残念ながら日本は含まれていません。 そのため、- セキュリティ問題への対応を除き、緊急のアップデートをする必要はない
- 第2世代AirPodsとApple Watchを組み合わせて使いたい場合
- iPhone/iPadおよびMacとのOSの更新頻度レベルを合わせたい場合
- セキュリティ問題にできる限り対応したい場合
watchOS5.2 アップデート後の不具合について
2019年3月28日17:00現在、 Apple Watch Series 3 42mmのwatchOSを5.2にアップデートしましたが、下記のような不具合・問題は発生していません。- 起動しなくなる
- 再起動を繰り返す
- 通信しない
- 利用できない
watchOS5.2のアップデートのサイズ、所要時間について
watchOS5.2のサイズ、所要時間は次の通りです。| 機種 | 現watchOS | サイズ | 全体 所要時間 | ダウンロード 所要時間 | インストール所要時間 |
|---|---|---|---|---|---|
| Apple Watch Series 3 42mm | 5.1.3 | 486MB | 90分 | 64分 | 26分 |
- Apple Watchが充電器に接続されていること
- Apple Watchが50%以上充電されていること
- Apple WatchとペアリングしているiPhoneが同一のWi-Fiに接続されていること
watchOS5.2の更新内容
公式サイト「watchOS 5 のアップデートについて」の「watchOS 5.2」には次のように記載されています。watchOS 5.2日本においては、まだ心電図Appや不規則な心拍き通知機能が利用できないため、第2世代のAirPodsに対応したいか否かがアップデートの判断基準の一つとなります。このアップデートには以下の新機能、改善、およびバグの修正が含まれます:
- 香港およびヨーロッパのいくつかの地域で、Apple Watch Series 4の“心電図” Appを利用可能。利用可能な地域については次のサイトをご覧ください: https://www.apple.com/jp/watchos/feature-availability/
- 香港およびヨーロッパのいくつかの地域で、“不規則な心拍の通知”を利用可能。利用可能な地域については次のサイトをご覧ください: https://www.apple.com/jp/watchos/feature-availability/
- 新しいAirPods(第2世代)に対応。
watchOS5.2のセキュリティアップデート内容
watchOS5.2では24件のセキュリティ問題に対応しています。 公式サイトの日本語版にはセキュリティアップデートについてwatchOS5.2の情報が含まれていないため、英語サイトの「About the security content of watchOS 5.2」の「watchOS 5.2」の情報を記載します。watchOS 5.2Released March 27, 2019 CFStringconfigd
- Available for: Apple Watch Series 1 and later
- Impact: Processing a maliciously crafted string may lead to a denial of service
- Description: A validation issue was addressed with improved logic.
- CVE-2019-8516: SWIPS Team of Frifee Inc.
Contacts
- Available for: Apple Watch Series 1 and later
- Impact: A malicious application may be able to elevate privileges
- Description: A memory initialization issue was addressed with improved memory handling.
- CVE-2019-8552: Mohamed Ghannam (@_simo36)
CoreCrypto
- Available for: Apple Watch Series 1 and later
- Impact: A malicious application may be able to elevate privileges
- Description: A buffer overflow issue was addressed with improved memory handling.
- CVE-2019-8511: an anonymous researcher
file
- Available for: Apple Watch Series 1 and later
- Impact: A malicious application may be able to elevate privileges
- Description: A buffer overflow was addressed with improved bounds checking.
- CVE-2019-8542: an anonymous researcher
Foundation
- Available for: Apple Watch Series 1 and later
- Impact: Processing a maliciously crafted file might disclose user information
- Description: An out-of-bounds read was addressed with improved bounds checking.
- CVE-2019-6237: an anonymous researcher
GeoServices
- Available for: Apple Watch Series 1 and later
- Impact: An application may be able to gain elevated privileges
- Description: A memory corruption issue was addressed with improved input validation.
- CVE-2019-7286: an anonymous researcher, Clement Lecigne of Google Threat Analysis Group, Ian Beer of Google Project Zero, and Samuel Groß of Google Project Zero
iAP
- Available for: Apple Watch Series 1 and later
- Impact: Clicking a malicious SMS link may lead to arbitrary code execution
- Description: A memory corruption issue was addressed with improved validation.
- CVE-2019-8553: an anonymous researcher
IOHIDFamily
- Available for: Apple Watch Series 1 and later
- Impact: A malicious application may be able to elevate privileges
- Description: A buffer overflow was addressed with improved bounds checking.
- CVE-2019-8542: an anonymous researcher
Kernel
- Available for: Apple Watch Series 1 and later
- Impact: A local user may be able to cause unexpected system termination or read kernel memory
- Description: A memory corruption issue was addressed with improved state management.
- CVE-2019-8545: Adam Donenfeld (@doadam) of the Zimperium zLabs Team
Kernel
- Available for: Apple Watch Series 1 and later
- Impact: A remote attacker may be able to cause unexpected system termination or corrupt kernel memory
- Description: A buffer overflow was addressed with improved size validation.
- CVE-2019-8527: Ned Williamson of Google and derrek (@derrekr6)
Kernel
- Available for: Apple Watch Series 1 and later
- Impact: A malicious application may be able to determine kernel memory layout
- Description: A memory initialization issue was addressed with improved memory handling.
- CVE-2019-8540: Weibo Wang (@ma1fan) of Qihoo 360 Nirvan Team
Kernel
- Available for: Apple Watch Series 1 and later
- Impact: An application may be able to gain elevated privileges
- Description: A logic issue was addressed with improved state management.
- CVE-2019-8514: Samuel Groß of Google Project Zero
Kernel
- Available for: Apple Watch Series 1 and later
- Impact: A malicious application may be able to determine kernel memory layout
- Description: An out-of-bounds read issue existed that led to the disclosure of kernel memory. This was addressed with improved input validation.
- CVE-2019-6207: Weibo Wang of Qihoo 360 Nirvan Team (@ma1fan)
- CVE-2019-8510: Stefan Esser of Antid0te UG
Messages
- Available for: Apple Watch Series 1 and later
- Impact: A local user may be able to read kernel memory
- Description: A memory corruption issue was addressed with improved memory handling.
- CVE-2019-7293: Ned Williamson of Google
Passcode
- Available for: Apple Watch Series 1 and later
- Impact: A local user may be able to view sensitive user information
- Description: An access issue was addressed with additional sandbox restrictions.
- CVE-2019-8546: ChiYuan Chang
Power Management
- Available for: Apple Watch Series 1 and later
- Impact: A partially entered passcode may not clear when the device goes to sleep
- Description: An issue existed where partially entered passcodes may not clear when the device went to sleep. This issue was addressed by clearing the passcode when a locked device sleeps.
- CVE-2019-8548: Tobias Sachs
Privacy
- Available for: Apple Watch Series 1 and later
- Impact: A malicious application may be able to execute arbitrary code with system privileges
- Description: Multiple input validation issues existed in MIG generated code. These issues were addressed with improved validation.
- CVE-2019-8549: Mohamed Ghannam (@_simo36) of SSD Secure Disclosure (ssd-disclosure.com)
Siri
- Available for: Apple Watch Series 1 and later
- Impact: A malicious app may be able to track users between installs
- Description: A privacy issue existed in motion sensor calibration. This issue was addressed with improved motion sensor processing.
- CVE-2019-8541: Stan (Jiexin) Zhang and Alastair R. Beresford of the University of Cambridge, Ian Sheret of Polymath Insight Limited
TrueTypeScaler
- Available for: Apple Watch Series 1 and later
- Impact: A malicious application may be able to initiate a Dictation request without user authorization
- Description: An API issue existed in the handling of dictation requests. This issue was addressed with improved validation.
- CVE-2019-8502: Luke Deshotels of North Carolina State University, Jordan Beichler of North Carolina State University, William Enck of North Carolina State University, Costin Carabaș of University POLITEHNICA of Bucharest, and Răzvan Deaconescu of University POLITEHNICA of Bucharest
WebKit
- Available for: Apple Watch Series 1 and later
- Impact: Processing a maliciously crafted font may result in the disclosure of process memory
- Description: An out-of-bounds read was addressed with improved bounds checking.
- CVE-2019-8517: riusksk of VulWar Corp working with Trend Micro Zero Day Initiative
WebKit
- Available for: Apple Watch Series 1 and later
- Impact: Processing maliciously crafted web content may lead to arbitrary code execution
- Description: A memory corruption issue was addressed with improved memory handling.
- CVE-2019-8536: Apple
- CVE-2019-8544: an anonymous researcher
WebKit
- Available for: Apple Watch Series 1 and later
- Impact: Processing maliciously crafted web content may lead to arbitrary code execution
- Description: A type confusion issue was addressed with improved memory handling.
- CVE-2019-8506: Samuel Groß of Google Project Zero
WebKit
- Available for: Apple Watch Series 1 and later
- Impact: Processing maliciously crafted web content may lead to arbitrary code execution
- Description: Multiple memory corruption issues were addressed with improved memory handling.
- CVE-2019-8518: Samuel Groß of Google Project Zero
- CVE-2019-8558: Samuel Groß of Google Project Zero
- CVE-2019-8559: Apple
- CVE-2019-8563: Apple
- Available for: Apple Watch Series 1 and later
- Impact: Processing maliciously crafted web content may result in the disclosure of process memory
- Description: A validation issue was addressed with improved logic.
- CVE-2019-7292: Zhunki and Zhiyi Zhang of 360 ESG Codesafe Team
Additional recognitionKernel
- We would like to acknowledge Brandon Azad of Google Project Zero for their assistance.
Information about products not manufactured by Apple, or independent websites not controlled or tested by Apple, is provided without recommendation or endorsement. Apple assumes no responsibility with regard to the selection, performance, or use of third-party websites or products. Apple makes no representations regarding third-party website accuracy or reliability. Risks are inherent in the use of the Internet. Contact the vendor for additional information. Other company and product names may be trademarks of their respective owners.公開日:
watchOS5.2へのアップデート手順と確認方法について
watchOS5.2へのアップデート手順
watchOS5.2へのアップデート手順は次のとおりです。 [timeline][tl label=’手順 1′ title=’Watchアプリの起動’] Apple WatchとペアリングしているiPhoneで「Watch」アプリをタップし起動します。 [/tl][tl label=’手順 2′ title=’一般の選択’]
マイウォッチ画面で画面をスクロールし「一般」をタップします。
[/tl][tl label=’手順 2′ title=’一般の選択’]
マイウォッチ画面で画面をスクロールし「一般」をタップします。
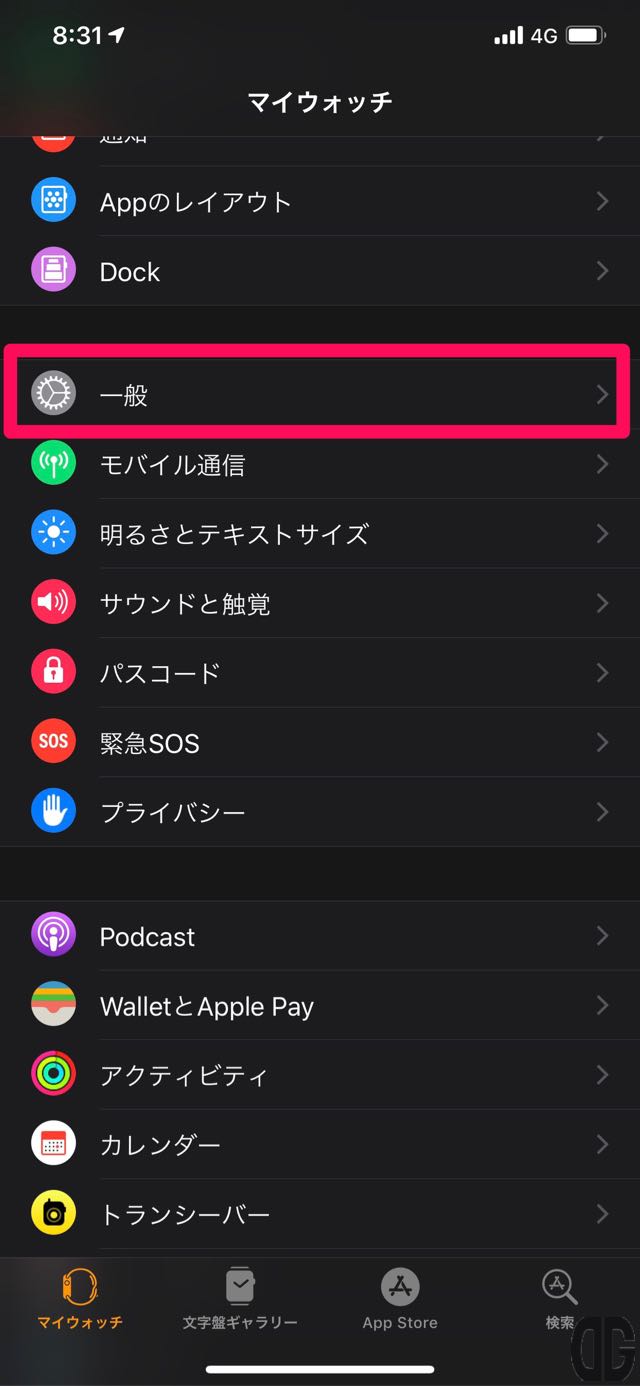 [/tl][tl label=’手順 3′ title=’ソフトウェア・アップデートの選択’]
一般画面で「ソフトウェア・アップデート」をタップします。
[/tl][tl label=’手順 3′ title=’ソフトウェア・アップデートの選択’]
一般画面で「ソフトウェア・アップデート」をタップします。
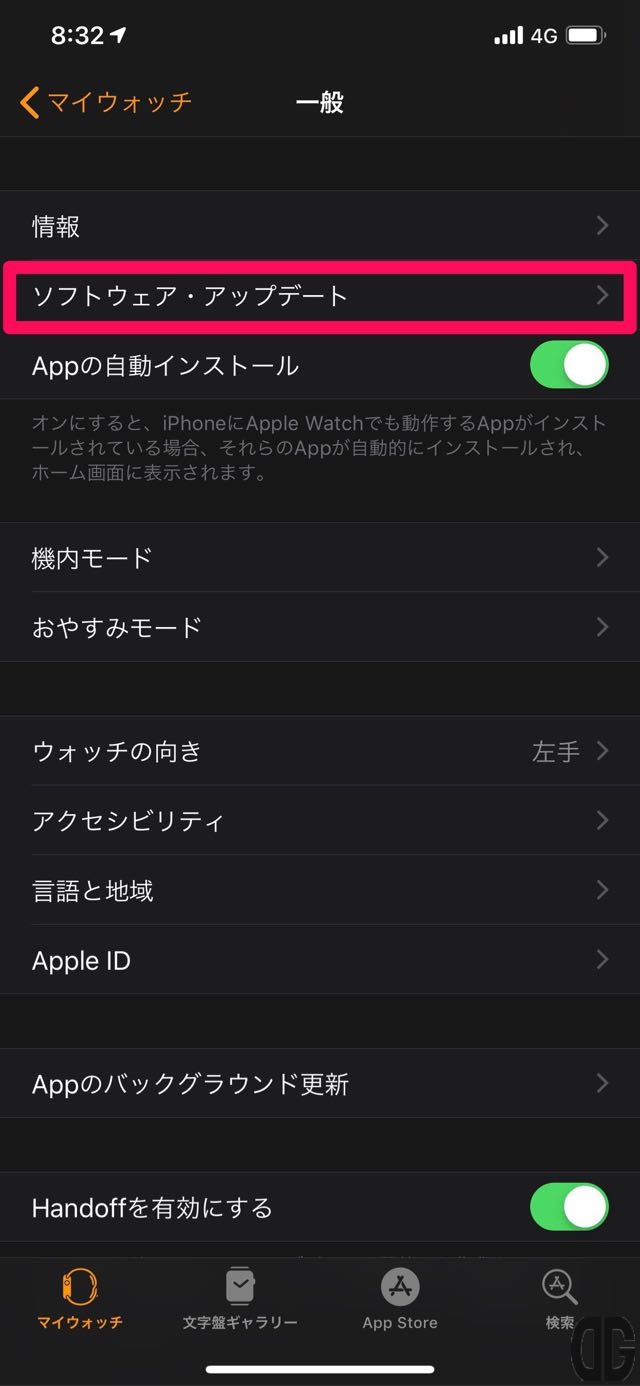 [/tl][tl label=’手順 4′ title=’ダウンロードとインストールの選択’]
ソフトウェア・アップデート画面で「watchOS 5.2」であること、ダウンロードサイズを確認し、「ダウンロードとインストール」をタップします。
[/tl][tl label=’手順 4′ title=’ダウンロードとインストールの選択’]
ソフトウェア・アップデート画面で「watchOS 5.2」であること、ダウンロードサイズを確認し、「ダウンロードとインストール」をタップします。
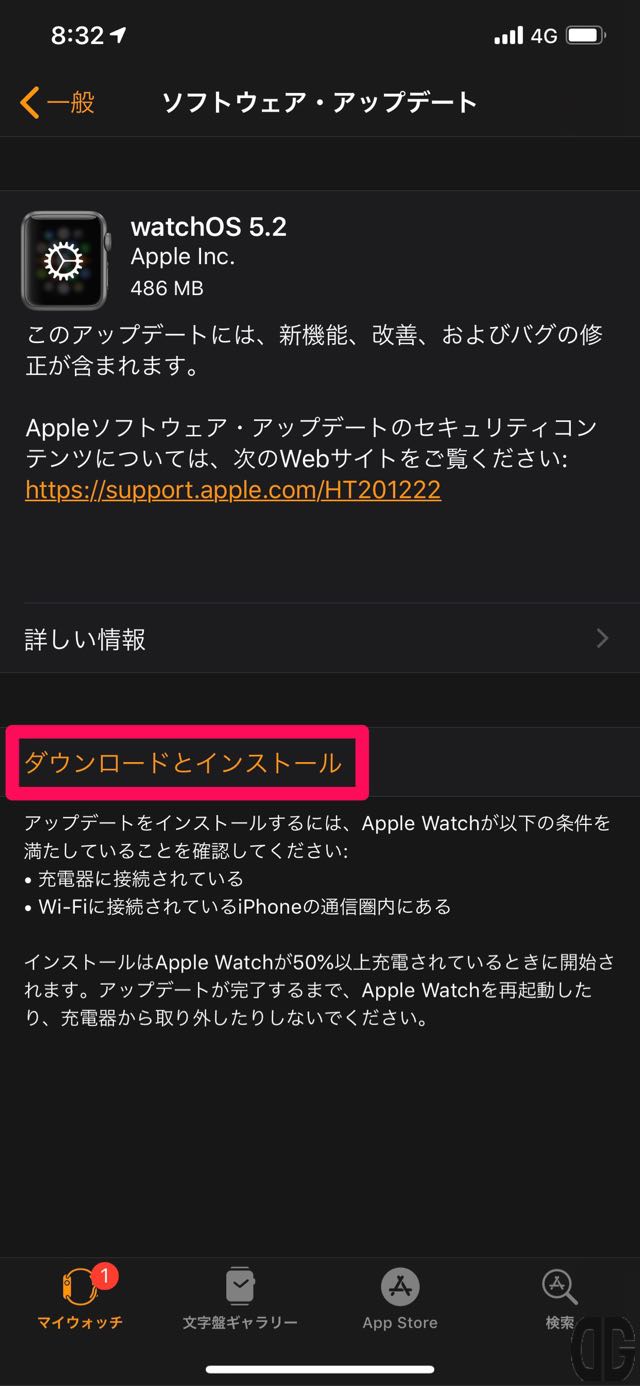 なお、「詳しい情報」をタップすると「このアップデートについて」画面が表示されます。
なお、「詳しい情報」をタップすると「このアップデートについて」画面が表示されます。
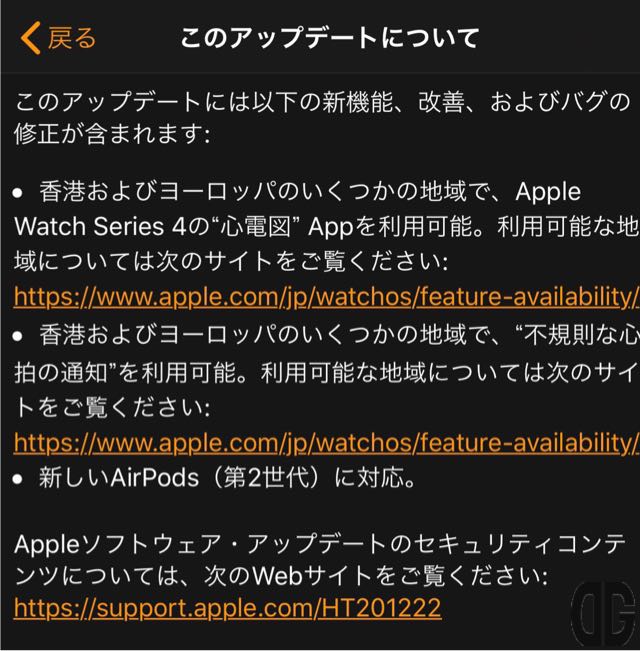 内容については前述の「watchOS5.2更新内容」と同じものとなります。
[/tl][tl label=’手順 5′ title=’バスコードの入力’]
パスコードを入力します。
内容については前述の「watchOS5.2更新内容」と同じものとなります。
[/tl][tl label=’手順 5′ title=’バスコードの入力’]
パスコードを入力します。
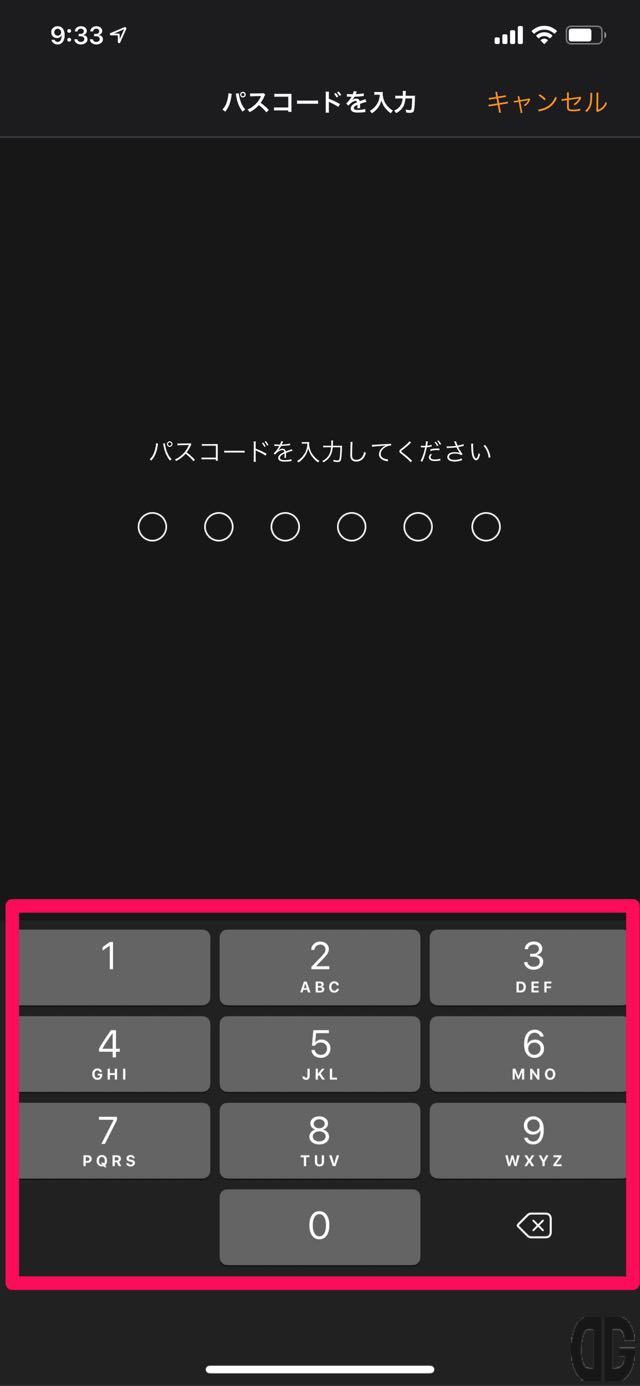 [/tl][tl label=’手順 6′ title=’ダウンロード、再起動、インストールの実施’]
自動的にiPhoneを経由してApple Watchにアップデートファイルがダウンロードされ、自動的に再起動、インストールが実施されます。
[/tl][tl label=’手順 6′ title=’ダウンロード、再起動、インストールの実施’]
自動的にiPhoneを経由してApple Watchにアップデートファイルがダウンロードされ、自動的に再起動、インストールが実施されます。
 [/tl][tl label=’手順 7′ title=’アップデートの終了’]
iPhoneからApple Watchにアップデートファイルが転送されると、iPhoneのWatchアプリ上では実際にApple Watchでのアップデートが終了する前に「watchOS 5.2 このソフトウェアは最新です。」と表示されます。
[/tl][tl label=’手順 7′ title=’アップデートの終了’]
iPhoneからApple Watchにアップデートファイルが転送されると、iPhoneのWatchアプリ上では実際にApple Watchでのアップデートが終了する前に「watchOS 5.2 このソフトウェアは最新です。」と表示されます。
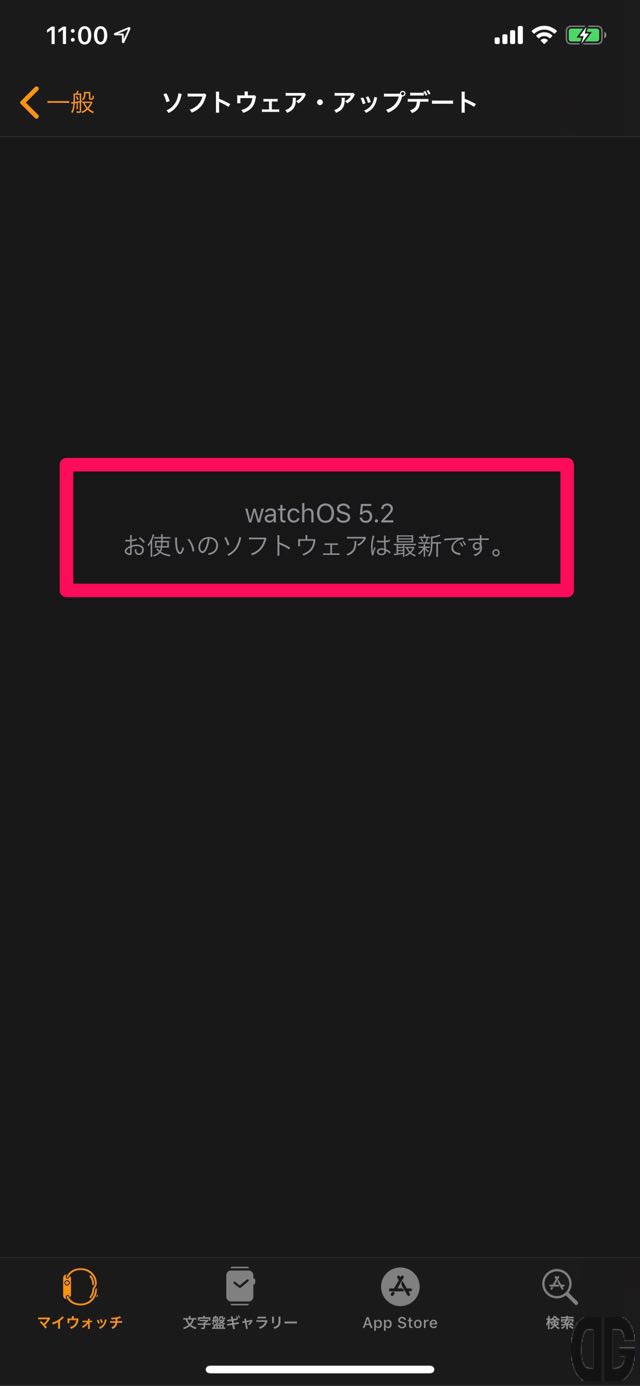 通常、Apple Watch上てはまだアップデートが実施されているため、Apple Watchに待受画面が表紙されるまで待ちます。
[/tl][tl label=’手順 8′ title=’アップデートの完了’]
Apple Watchに待受画面が表示されることを確認します。
[/tl][tl][/tl][/timeline]
以上で、watchOS 5.2へのアップデートは完了です。
通常、Apple Watch上てはまだアップデートが実施されているため、Apple Watchに待受画面が表紙されるまで待ちます。
[/tl][tl label=’手順 8′ title=’アップデートの完了’]
Apple Watchに待受画面が表示されることを確認します。
[/tl][tl][/tl][/timeline]
以上で、watchOS 5.2へのアップデートは完了です。
watchOS5.2にアップデートされたことの確認
Apple Watchに待受仮面が表示されればwatchOS 5.2へのアップデートは完了しています。 が、iPhoneやApple Watchでアップデートされたことを確認するには次の手順で確認します。iPhoneのWatchアプリでの確認
[timeline] [tl label=’手順 1′ title=’iPhoneでWatchアプリを起動’][/tl] [tl label=’手順 2′ title=’一般を選択’][/tl] [tl label=’手順 3′ title=’ソフトウェア・アップデートを選択’] ソフトウェア・アップデート画面に「watchOS 5.2 このソフトウェアは最新です。」と表示されることを確認します。 [/tl][tl label=’手順 4′ title=’情報を選択’]
一般に戻り「情報」を選択します。
情報画面の「バージョン」に「5.2 (16T225)」と表示されることを確認します。
[/tl][tl label=’手順 4′ title=’情報を選択’]
一般に戻り「情報」を選択します。
情報画面の「バージョン」に「5.2 (16T225)」と表示されることを確認します。
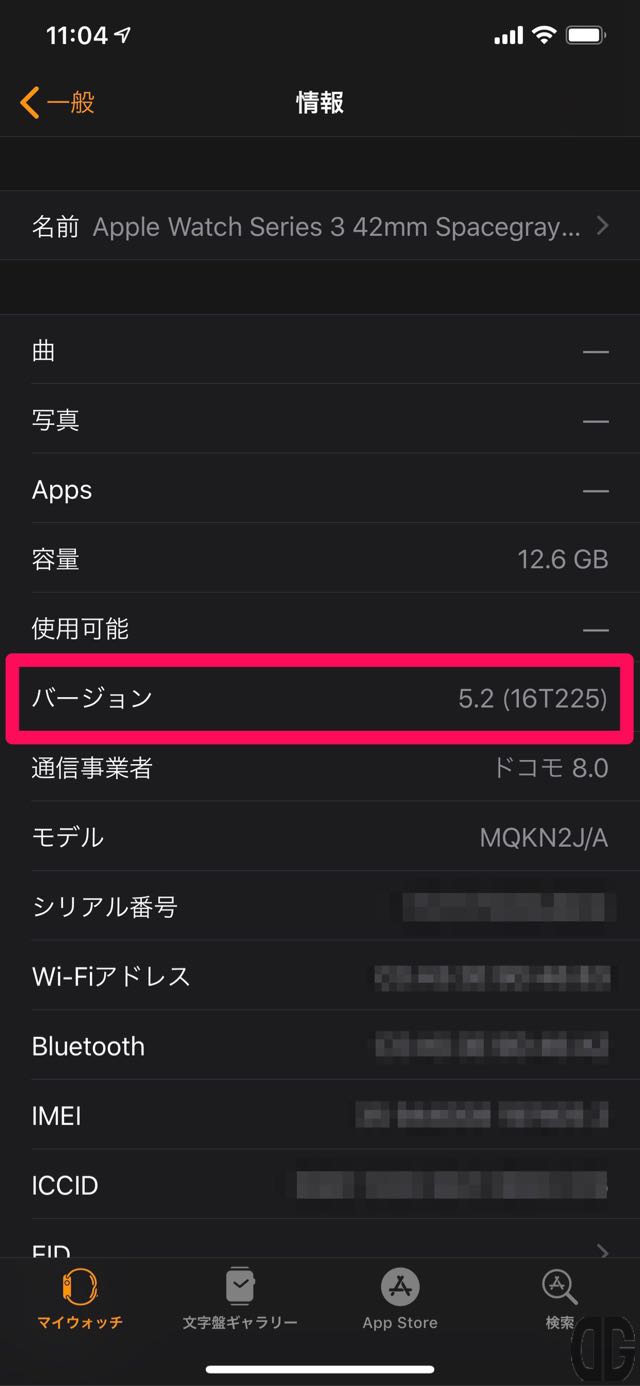 [/tl][tl][/tl][/timeline]
[/tl][tl][/tl][/timeline]
Apple Watchの「設定」アプリでの確認
Apple Watchの「設定」アプリでもwatchOS 5.2にアップデートされたことを確認できます。 [timeline] [tl label=’手順 1′ title=’Apple Watchで設定アプリを起動’][/tl] [tl label=’手順 2′ title=’一般を選択’][/tl] [tl label=’手順 3′ title=’情報を選択’] Apple Watchの画面をスクロールし、「バージョン」に「5.2 (16T225)」と表示されることを確認します。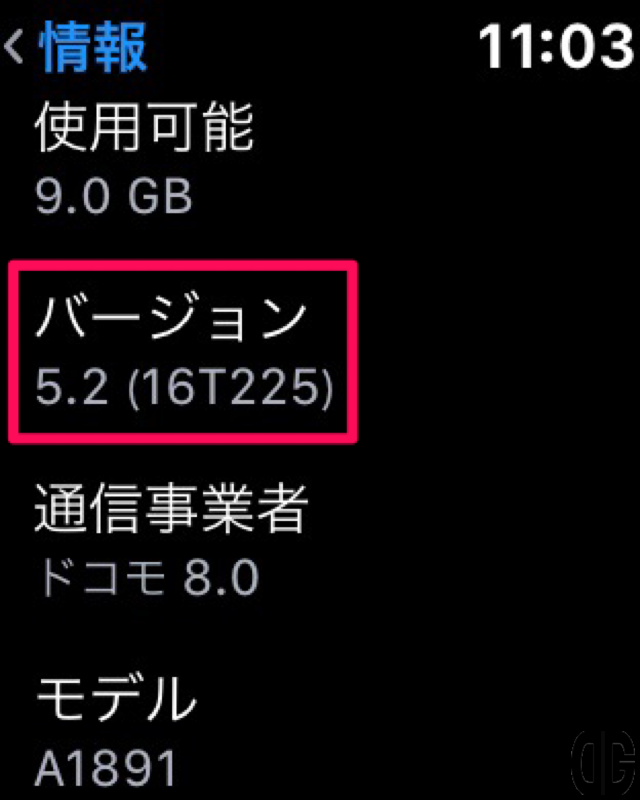 [/tl][tl][/tl][/timeline]
[/tl][tl][/tl][/timeline]


